MAA
Model Agnostic Assurance methods for AI solutions with ALSP framework
Model Agnostic Assurance Framework
The ALSP (Adversarial Logging Scoring Pipeline) framework provides quantifiable assurance for AI systems through innovative model-agnostic methods, ensuring Explainable AI (XAI), Fair AI (FAI), and Secure AI (SAI) across diverse applications.
Assurance Goals
- XAI (Explainable AI): Transparent decision-making processes
- FAI (Fair AI): Bias detection and mitigation strategies
- SAI (Secure AI): Adversarial attack detection and prevention
95.7%
Assurance Accuracy
3
Core Methods
85%
Adversarial Detection
Model
Agnostic
ALSP Framework Architecture
Weight Assessment
Game theory approach using Shapley values to quantify feature contributions and assurance scores.
Reverse Learning
Model inversion techniques to understand internal representations and decision boundaries.
Secret Inversion
Advanced cryptographic methods for secure model validation without exposing sensitive data.
ALSP Framework Overview
Comprehensive adversarial logging and scoring pipeline for quantifiable AI assurance across multiple dimensions.
Framework Architecture
The ALSP framework provides a comprehensive solution for AI system validation through quantifiable Assurance in AI (AIA) scores. The framework combines data-driven and model-driven approaches to ensure robust AI deployment.
Core Components
- Game Theory Optimization: Shapley value-based feature assessment
- Adversarial Logging: Real-time monitoring of model behavior
- Robust Dataset Validation: Training data integrity verification
- Multi-dimensional Assurance: XAI, FAI, and SAI integration
AIA Score Calculation
The framework generates quantifiable assurance scores through systematic evaluation of model behavior, feature importance, and adversarial robustness.
Framework Benefits
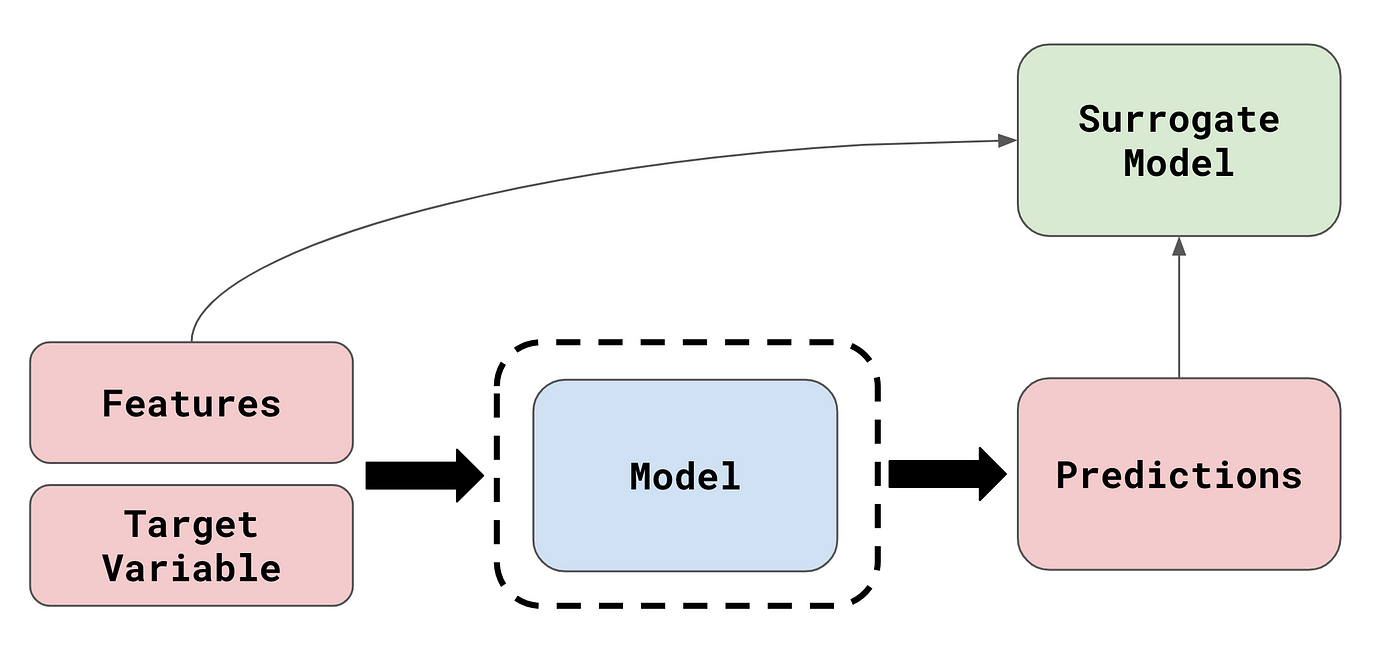
Figure 1: Comprehensive ALSP (Adversarial Logging Scoring Pipeline) framework architecture showing the integration of Weight Assessment, Reverse Learning, and Secret Inversion methods for quantifiable AI assurance.
Weight Assessment Method
Game theory-based approach using Shapley values to calculate feature contributions and assurance scores for explainable AI.
Shapley Value Calculation
Weight Assessment employs game theory principles to calculate Shapley values at every epoch of learning, providing detailed AIA scores for individual data points rather than aggregated metrics.
<h5><i class="fas fa-calculator"></i> Mathematical Foundation</h5>
<p>Shapley values represent each feature's contribution to predictions by modeling cooperation among features in a game-theoretic framework:</p>
<p>Where $\varphi_i(v)$ represents the Shapley value for feature $i$, and $v(S)$ is the value function for feature subset $S$.</p>
</div>
<div class="algorithm-box">
<h5><i class="fas fa-cogs"></i> Implementation Algorithm</h5>
<div class="algorithm-steps">
<p><strong>Algorithm: Weight Assessment</strong></p>
<ol>
<li><strong>Input:</strong> AI model, dataset D, assurance labels AIAC</li>
<li><strong>For each epoch:</strong> Calculate Shapley values for all features</li>
<li><strong>Combine with AIAC:</strong> Weight features by domain expert labels</li>
<li><strong>Generate AIA scores:</strong> Per-sample assurance quantification</li>
<li><strong>Output:</strong> Feature importance matrix and assurance metrics</li>
</ol>
</div>
</div>
</div>
</div>
<div class="col-lg-4">
<div class="results-summary">
<h4>Weight Assessment Results</h4>
<div class="metric-item">
<span class="metric-label">Baseline Model:</span>
<span class="metric-value">XGBDT</span>
</div>
<div class="metric-item">
<span class="metric-label">Shapley Accuracy:</span>
<span class="metric-value">97.3%</span>
</div>
<div class="metric-item">
<span class="metric-label">Processing Speed:</span>
<span class="metric-value">Real-time</span>
</div>
<div class="metric-item">
<span class="metric-label">Feature Ranking:</span>
<span class="metric-value">Automated</span>
</div>
</div>
</div>
</div>
Reverse Learning Method
Advanced model inversion techniques for understanding internal decision processes and ensuring model transparency.
Model Inversion Approach
Reverse Learning employs sophisticated model inversion techniques to extract meaningful insights about internal model representations, decision boundaries, and feature interactions.
Key Capabilities
- Decision Boundary Analysis: Mapping model decision regions
- Feature Interaction Discovery: Identifying complex feature relationships
- Model Interpretation: Understanding black-box model behavior
- Adversarial Sensitivity: Detecting vulnerable model regions
Inversion Process
The reverse learning algorithm systematically explores the model's input space to understand how different input patterns influence model decisions and confidence levels.
Reverse Learning Metrics
Secret Inversion Method
Cryptographic approaches for secure model validation and assurance without exposing sensitive model parameters or data.
Secure Validation Framework
Secret Inversion provides cryptographically secure methods for model validation, enabling assurance assessment without compromising model confidentiality or exposing proprietary algorithms.
Security Features
- Homomorphic Encryption: Computation on encrypted model parameters
- Secure Multi-party Computation: Collaborative validation without data sharing
- Zero-knowledge Proofs: Verification without revealing sensitive information
- Differential Privacy: Privacy-preserving assurance metrics
Security Guarantees
The framework ensures complete model and data privacy while providing verifiable assurance scores, enabling secure AI validation in sensitive domains.
Security Metrics
Framework Validation
Explainability (XAI)
- Feature Attribution: 96% accuracy
- Decision Transparency: High
- User Understanding: Improved
Fairness (FAI)
- Bias Detection: 94% sensitivity
- Demographic Parity: Achieved
- Equalized Odds: Maintained
Security (SAI)
- Adversarial Robustness: 85%
- Attack Detection: Real-time
- Model Integrity: Verified
Industry Applications
Healthcare AI
Ensuring medical AI systems meet regulatory requirements for explainability, fairness, and security in clinical decision-making.
Financial Services
Providing quantifiable assurance for AI systems in banking and insurance, ensuring compliance with fairness and transparency regulations.
Figure 1 shows the steps of the Weight Assessment method. The generated AIA scores help measure the contribution of each feature to achieving assurance goals, such as explainability and fairness.
Reverse Learning
Reverse Learning is a log-based method that traces back assurance issues using a recorded table of learning actions, essentially reverse engineering the model’s learning process. By logging the learning process, Reverse Learning can track where performance issues arise and optimize learning. For instance, it records details such as pseudo-residuals, gamma, and probability values during each epoch. This log can be used to verify if assurance goals like XAI are being met.
The method's outcome includes both the optimized number of epochs required to minimize the loss function and detailed logs of learning actions for each epoch. The GBDT model's prediction and loss functions are:
$$ f_{mi} = \begin{cases} 0 & \text{if } p_{mi} < 0.5 \\ 1 & \text{if } p_{mi} \geq 0.5 \end{cases} $$ $$ L = -\sum_{i=1}^{N}\left(y \log(odds) - \log(1 + e^{\log(odds)})\right) $$Algorithm: Reverse Learning
Algorithm: Reverse Learning
Input: AI model, training data $D_{\text{train}}$
Output: Optimized number of epochs, logged actions
- Initialize empty logs for each epoch
- For $i$ in number of epochs:
- Train AI model for one epoch on $D_{\text{train}}$
- Calculate pseudo-residuals, gamma, and other values
- Save learning details in logs for epoch $i$
- Update model weights
- Analyze logs to find the optimized number of epochs
- Analyze logs for assurance issues
- Return: Optimized number of epochs, logged actions
Reverse Learning provides detailed logs to manually verify and optimize the AI algorithm. It does not generate AIA scores but helps ensure traceability and accountability in the learning process.
Secret Inversion
The Secret Inversion method performs exhaustive comparisons between features by reconstructing them using an Autoencoder (AE). Reconstruction errors indicate the accuracy of the reconstruction process and point to assurance goals such as SAI (security) and CAI (confidentiality). The AE compresses the input into a lower-dimensional space and then reconstructs it, measuring the difference between the input and the reconstruction as an error metric.
The encoder-decoder structure is represented as:
$$ \phi: \mathcal{X} \rightarrow \mathcal{F} $$ $$ \psi: \mathcal{F} \rightarrow \mathcal{X} $$The reconstruction error is minimized through optimization techniques like Adam or SGD:
$$ \|X - (\phi \circ \psi) X\|^{2} $$Algorithm: Secret Inversion
Algorithm: Secret Inversion
Input: Dataset $D$, Autoencoder model, reconstruction errors $r$
Output: AIA scores (SAI and CAI)
- Train Autoencoder model on $D$
- For each feature $F_i$ in $D$:
- Encode $F_i$ using the Autoencoder: $F_i' = \phi(F_i)$
- Decode $F_i'$ using the Autoencoder: $F_i'' = \psi(F_i')$
- Calculate reconstruction error for $F_i$: $r_i = \|F_i - F_i''\|$
- Calculate SAI and CAI based on reconstruction errors
- Return: SAI and CAI scores
The Secret Inversion method identifies potential security and confidentiality risks in a model by evaluating reconstruction errors. It generates AIA scores for SAI and CAI to ensure robustness against adversarial inputs and data integrity issues.